In the previous blog, we learned about the OWASP API Security Top 10 API3:2019 Excessive Data Exposure with Example. In this blog, we will learn about the OWASP API Security Top 10 API4:2019 Lack of Resources & Rate Limiting, its impact, an example, and remediation.
What is Lack of Resources & Rate Limiting?
The rate limit refers to the number of API requests that a client can make within a set period of time, while the resource limit refers to the maximum file size that a client can upload via an API endpoint.
Impact
Suppose Resources & Rate Limit are not configured. In that case, the attacker may be able to send multiple concurrent requests from a single local computer or use cloud resources, which may lead to Denial of Service (DoS) because API requests will consume storage, CPU power, and network resources.
The attacker can also perform brute force attack if the rate limit is not properly set in the login API endpoint.
How to check if the API is vulnerable to Lack of Resources & Rate Limiting
- If there is no execution timeout set on the API Requests
- If maximum allocated memory is not set for each API request
- If the number of file descriptors is not, that allows us to limit the resources consumed by the process
- If the Number of processes limit is not set
- If the payload size limit is set
- If the number of requests per second accepted by the server is not set
- If the number of records per page to return in a single request response is not set
Example of Lack of Resources & Rate Limiting
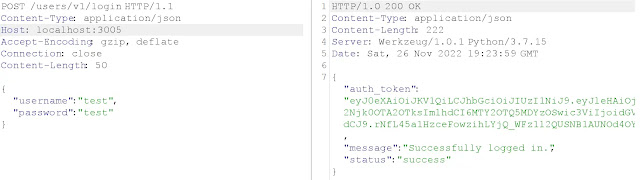
For example, I have one POST method-based API endpoint that takes user credentials as input and returns an authentication token that will be used to call other API endpoints that require authentication.
To check if the API is vulnerable to Lack of Resources & Rate Limiting, we will conduct a brute force attack on the password parameter using a wordlist that contains common passwords.
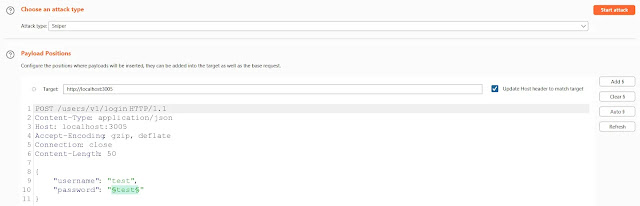
To conduct the brute-force attacker, we will send the request to the burp suite intruder and add password parameter values as payload position.
To conduct the brute-force attacker, we will send the request to the burp suite intruder and add password parameter values as payload position.
Now we will go to the payload section and paste the common password wordlist.
After loading the payload, click on the start attack button.
By default, the burp suite will send 10 requests per second.
As we can see in the above image, the intruder can send requests without any delay or restriction, which means that the login API endpoint is vulnerable to Lack of Resources & Rate Limiting.
If we sort the results by length, we can see that on test payload length is maximum, it means the test is the password.
Remediation
- Use docker to deploy API service because, in docker, it is easy to limit memory, CPU, Storage, etc.
- Implement the limit on the number of requests per second accepted by the server
- Define the maximum length for strings, the maximum number of elements in arrays, and the maximum size of the file accepted by the API service.
- Limit the number of records per page to be returned in a single request