In the previous blog, we learned about the OWASP API Security Top 10 API7:2019 Security Misconfiguration with Example. In this blog, we will learn about the OWASP API Security Top 10 API8:2019 Injection, its impact, an example, and remediation.
What is injection?
An injection vulnerability allows a malicious actor to inject malicious code into an API via direct input, parameters, headers, or integrated services, which could compromise the backend system and other clients connected to the application.
There are various injection vulnerabilities like SQL injection, Command Injection, XML External Entity, Cross-Site scripting, and so on.
Injection vulnerability can lead to sensitive information disclosure, DoS, or Complete system takeover.
APIs are vulnerable to injection vulnerabilities if:
- Input data is not validated, filtered, or sanitized by API
- Input data is directly used in database queries, System Commands, or XML parsers
- Data Input from external sources (integrated services) is not validated, filtered, or sanitized by API
Example
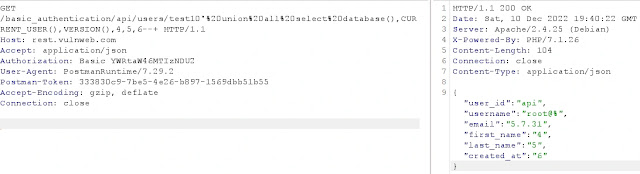
We have one API endpoint that takes the username as input and, in response, returns the details about the user.
Here the input passed in the username parameter is used in the database query to fetch the user details from the database.
So we check whether API is vulnerable to SQL injection or not because the username parameter is linked to the database.
When I pass username concatenated with malicious character (‘), then in response, we get the SQL syntax error indicating that the application may be vulnerable to SQL injection
Now we will try to balance the SQL query using SQL comment (--+)
Now that our SQL query is balanced, we will use SQL injection payload to get the database name, current user, and database version.
Remediation
- Perform data validation
- Escape special characters
- Validate, filter, and sanitize all input data
- Parameters datatypes must be defined

.webp)