In the previous blog, we learned about the OWASP API Security Top 10 API6:2019 Mass Assignment with Example. In this blog, we will learn about the OWASP API Security Top 10 API7:2019 Security Misconfiguration, its impact, an example, and remediation.
What is security misconfiguration?
Vulnerabilities can arise when security configurations of applications or systems have not been implemented, or Someone implemented them incorrectly. Such vulnerabilities may include unpatched or vulnerable components, unprotected sensitive configuration files, and default security configurations.
Improperly configured security settings can make user information vulnerable and system details that may result in a complete server takeover.
Improperly configured security settings can make user information vulnerable and system details that may result in a complete server takeover.
APIs are vulnerable to security misconfiguration if:
- Any vulnerable or unpatched application, system, or server used by APIs
- Sensitive Directories or files are unprotected
- We have not hardened OS
- TLS is not implemented or misconfigured
- An unnecessary HTTP method is enabled
- Application response with stack traces or other sensitive information
- improperly configured permissions on cloud services
- Improper CORS policy configuration
Example:
- During reconnaissance, the attacker found the hidden API endpoint that developers and DevOps use to get the debug logs that contain sensitive information.
- After conducting the port scanning attacker found the application is using an outdated and vulnerable database with default credentials.
Demo
Now we will see a demo of Security misconfiguration in APIs.
We have 3 API endpoints
- POST /vapi/api7/user - To create a new user (Response Contain userID)
- GET /vapi/api7/user/login - To login into the application (Response contains Session ID)
- GET /vapi/api7/user/key - To get the Authentication Key
First, we will create a new user
We will now log in to the application by providing the Authorization Token (base64 encoded value of username:password) in order to retrieve the Session ID.
base64_encode(demo:demo) = ZGVtbzpkZW1v
base64_encode(demo:demo) = ZGVtbzpkZW1v
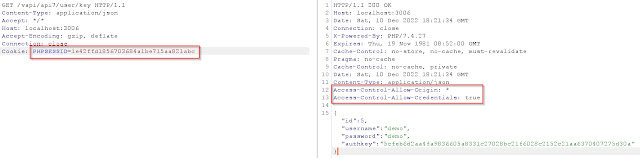
Now we will Utilize the Session ID to obtain the Authentication key.
As you can see in the above image, the response headers contain
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: true
Access-Control-Allow-Credentials: true
The above headers inculcate that the CORS policy is not configured correctly because Access-Control-Allow-Credentials is set to true, and Access-Control-Allow-Origin is set to wildcard.
Remediation
- Repeatable hardening process to deploy a secure environment
- Implement CORS policy correctly
- Establish secure communication for all APIs
- Review and update configurations
- Unnecessary HTTP methods must be disabled
- Automated scanning to test the configurations and settings

.webp)